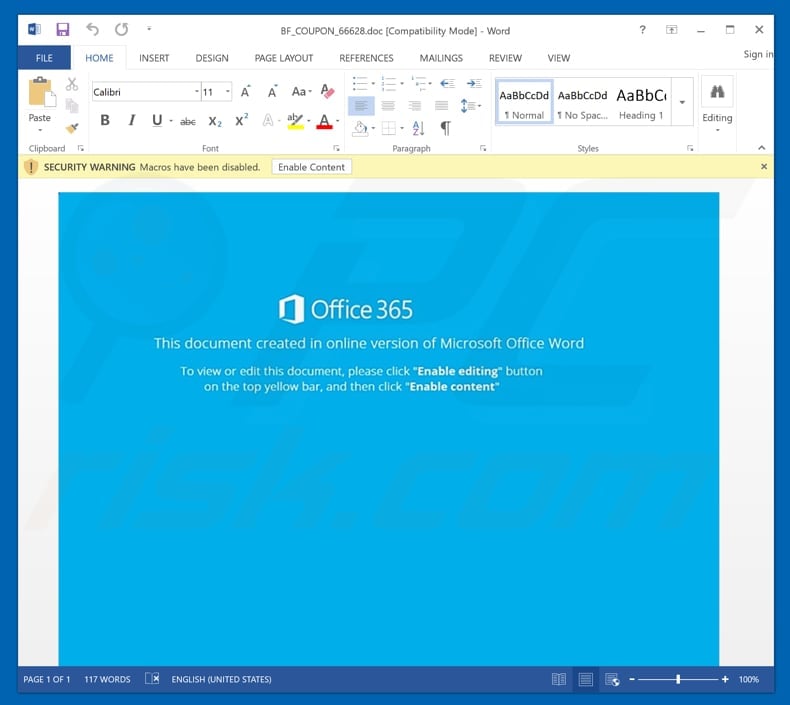
Remove File Virus Doc.blower
Feb 04, 2019 Before a file is encrypted, the.Blower ransomware virus makes a copy of this file, encrypts it, and then deletes the original file. This can allow you to recover your photos, documents and music using file restore apps like PhotoRec. Download PhotoRec on your computer by clicking on the following link. For that, you should download and install anti-malware that recognizes the PUP. Unlike when trying to get rid of the threat yourself, security software can detect all the malicious files within the system and remove the privileges Segurazo established for itself during the installation process.
July 24, 2020
Save up to $65 on Norton 360 for first year*
Get multiple layers of protection for your Cyber Safety. Don't wait!
Does my Android phone have a virus? Is it infected with malware or a malicious app? Will my personal information be held for ransom? If you find yourself asking these questions, then here is some useful information about Android devices and antivirus apps that may help you.
Viruses and other types of malware
Malware is malicious software that can sneak onto your phone. Written with the intent to cause harm, malware can include viruses, computer worms, Trojans, ransomware, and spyware.
Cybercriminals can use malware to access your personal data and, in some cases, subsequently use that sensitive information to commit identity theft or fraud.
Viruses are a particular type of malware that infiltrate a computer or other device and their programs. A cybercriminal may be able to install a virus on your device without your knowledge or consent. The virus may then be able to insert new, malicious code on your device that can monitor and manipulate your online activity.
What can viruses and other malware do to Android phones?
Malware is designed to generate revenue for cybercriminals.
Malware can steal your information, make your device send SMS messages to premium rate text services, or install adware that forces you to view web pages or download apps.
Info stealers can steal your contact list, your personal information, your location, your passwords, and more.
With the aid of malware, cybercriminals can access your devices and steal your information for their own use or to sell on the dark web.
Hackers also use ransomware to lock devices and encrypt personal data. Then they can demand a ransom payment from the victim in order to regain access to their files.
Signs your Android phone may have a virus or other malware
Phones can be vulnerable to damage externally and internally. While the external damage is usually visible, internal damage is usually hidden from view.
Malware like viruses are known to perform repeated tasks that can take up resources on your devices. Signs of malware may show up in these ways.
- Your phone is too slow.
- Apps take longer to load.
- The battery drains faster than expected.
- There is an abundance of pop-up ads.
- Your phone has apps you don’t remember downloading.
- Unexplained data usage occurs.
- Higher phone bills arrive.
How to check for viruses and other malware on your Android phone
A good way to check for malware on your Android phone is to run an antivirus scan.
Before buying antivirus software for your phone, make sure you consider the most comprehensive product that’s available for your device.
There are many antivirus software choices available on the market. Some are free, and some are sold.
It’s a good idea to do your research to ensure the security software you invest in runs a complete scan and doesn’t overlook any vulnerabilities. An incomplete scan could give you a false sense of security when, in fact, your device could be vulnerable to cyberattacks.
Norton Mobile Security for Android is one product you might consider.
How to remove viruses and other malware from your Android device
If you think you have malware on your phone, it’s important to stop the malware from causing any further damage. Here are a few steps you can take.
- Power off the phone and reboot in safe mode. Press the power button to access the Power Off options. Most Android phones come with the option to restart in Safe Mode. Here’s how, according to Google, although Safe Mode can vary by phone: Press your phone's power button. When the animation starts, press and hold your phone's volume down button. Hold it until the animation ends and your phone restarts. You'll see “Safe mode” at the bottom of your screen.
- Uninstall the suspicious app. Find the app in Settings and uninstall or force close it. This may not completely remove the malware, but it could prevent further damage to your device, or from it transmitting the malware to other devices on your network.
- Look for other apps you think may be infected. There’s a chance that some apps may have been infected by the malware. If you think you can identify those apps, delete them immediately.
- Install a robust mobile security app on your phone.
Tips to help protect your Android device against viruses and other malware
Here are seven key steps you can take to help protect against future risks.
- Invest in and use robust security software to protect your Android device.
- Keep all operating systems and software updated with the latest versions.
- Don’t click on suspicious or unfamiliar links in emails and text messages.
- Use strong, complicated passwords or a password manager.
- Never use unsecure Wi-Fi connections. Always use a VPN when connecting to public Wi-Fi.
- Always use strong cyber safety protection on all devices that connect to the internet.
- Always install apps from trusted sources, such as the Google Play Store. Read the fine print and permissions on the apps to understand how much access you are giving the app developers.
It’s a good idea to not wait until your device gets infected. Make protecting your Android device a priority. Having good antivirus software that helps protect your PCs, tablets, and other Android devices could help prevent malware from spreading from device to device.
Save up to $65 on Norton 360 for first year*
Get multiple layers of protection for your Cyber Safety. Don't wait!
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2020 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.

Viruses may attack files/folders, storage devices, or Windows operating systems. To remove a virus from an infected USB drive, SD card, pen drive and more on a Windows 10 computer, you can use CMD to get things done. If the virus delete or hide your files, don't hesitate to use EaseUS Data Recovery Wizard to recover them with ease.
On this page, we include four practical methods to help you remove viruses and help you restore virus removed or deleted files with powerful EaseUS file recovery software. If you are in this dilemma, follow fixes here to clean up virus and bring your files back:
| Workable Solutions | Step-by-step Troubleshooting |
|---|---|
| Fix 1. Remove Virus with CMD | Run Command Prompt as Administrator or EaseUS M Tool > Clear virus with attrib -s -h -r /s /d *.* command...Full steps |
| Fix 2. Run Antivirus | Run installed antivirus software, execute clean operation if virus is detected...Full steps |
| Fix 3. Run Windows Defender | Go to Settings > 'Update & Security' > 'Windows Security' > 'Virus & threat protection' ...Full steps |
| Fix 4. Format Infected Device | If the hard drive partition or external storage device was infected by virus, formatting it can help...Full steps |
| Bonus Tip. Recover Files | If files get hidden or deleted by the virus, run EaseUS Data Recovery Wizard > Scan device and recover...Full steps |
What Damage Could Viruses Do
We loathe computer viruses, undoubtedly. But do you know exactly how viruses can damage your computer? There are many types of viruses, and they behave in different ways. To sum it up, a computer virus is simply a type of program that causes your computer to act in an undesirable way. It can be a dangerous infiltration designed to drag your computer down, erase important files, track your habits, or gives hackers access to your personal information... A virus is a great nuisance. Some viruses like the Locky virus and CryptoLocker, also known as ransomware, delete computer files, encrypt them, even change the file extension to .locky or .encypt. Other viruses hide files and leave users with nowhere to unhide them.
It's certainly true that a virus is something you will want to remove once you find it. Among the multiple choices, many users attempt to remove viruses using CMD.
Why Can You Remove a Virus Using CMD
In fact, using command lines doesn't directly check and remove viruses from your computer or external storage device. CMD helps to achieve your goal of removing viruses by showing the hidden viruses on a partition or drive. Afterward, you can delete the suspicious files. Since viruses always conceal themselves, you need to make them appear and then delete the virus files. Then how can you show the potentially hidden virus files using CMD? All you need is the attrib command.
The attrib command is a Command Prompt command used to display, set, or remove the attributes of the files or folders in the selected location. By canceling the 'hidden' attribute of the virus, you can see it appearing in the folder. And then you will know where to find and remove it.
How to Remove Virus Using CMD
Now, follow the steps below to delete viruses from your computer or storage device using CMD.
Step 1. Type cmd in the search bar, right-click 'Command Prompt' and choose 'Run as an administrator'.
Step 2. Type F: and press 'Enter'. (Replace 'F' with the drive letter of the infected partition or device.)
Step 3. Type attrib -s -h -r /s /d *.* and hit 'Enter'.
Step 4. Type dir and hit 'Enter'. Now you will see all the files under the assigned drive. (The dir command displays a list of a directory's files and subdirectories.)
Step 5. For your information, a virus name may contain words like 'autorun' and with '.inf' as the extension. Thus, if you find such suspicious files, type del autorun.inf to remove the virus.
Here are the basic attributes of the 'attrib' command:
Email Worm Virus
R – represents the 'Read-only' attribute of a file or folder. Read-only means the file cannot be written on or executed.
H – the 'Hidden' attribute.
A – stands for 'Archiving' which prepares a file for archiving.
S – the 'System' attribute changes the selected files or folders from user files into system files.
I - 'not content indexed file' attribute.
The 'attrib' Syntax:
ATTRIB [+ attribute | – attribute] [pathname] [/S [/D]]
In the above command, let's see what the different parameters and switches are:
'+ / –': To enact or to cancel the specified attribute.
'attribute': As explained above.
'/S': Searching throughout the entire path including subfolders.
'/D': Include any process folder.
'pathname': Path where the target file or folder is located.
Here is the proper syntax order for attrib command:
ATTRIB [+R | -R] [+A | -A ] [+S | -S] [+H | -H] [+I | -I] [drive:][path][filename] [/S [/D] [/L]]
- Warning
- Be careful while using the Command Prompt. Improper use of cmd can result in system damage.
If you receive the message 'Access denied', you should:
- Make sure you have run Command Prompt as an administrator
- Make sure the file/folder is not in use
- Check the permission of the current account and make sure you have full control over the file/folder (right-click the file/folder/partition and go to 'Security')
- Use CHKDSK command to check for file system errors (run Command prompt and enter chkdsk /f [drive letter]:)
Manual input of the command line is suitable for computer professionals since wrong commands can cause more severe problems. Therefore, for security and usability, we strongly recommend you try an automatic command line alternative. EaseUS Tools M is a practical tool that enables you to check and fix files system error, enable/disable write protection and system update with one-click instead of typing intricate command lines.
Follow the simple steps below to show hidden files with this 1-click-fix software.
Step 1. DOWNLOAD EaseUS Tools M for Free.
Step 2. Start EaseUS Tools M, choose 'File Showing' on the left pane. Next, choose the target drive for scanning.
Step 3. After the operation completes, click the View button to check the hidden files.
3 Other Ways to Remove Virus
In addition to using CMD, there are other methods available to remove a virus from your computer or storage device, like using antivirus software, Windows Defender, and formatting the storage device.
Method 1. Run Antivirus
Almost every computer has antivirus software installed. Whenever you find your computer is infected by a virus, running the antivirus software may help.
Method 2. Run Windows Defender Antivirus
Windows Defender Antivirus is the built-in antivirus protection in Windows 10. It provides protection against viruses, malware, and spyware for your computer and connected devices. If you don't have third-party antivirus software, using the built-in utility is advisable.
Step 1. Go to 'Settings' > 'Update & Security' > 'Windows Security'.
Step 2. Click 'Virus & threat protection'.
Remove File Virus Doc.blower Windows 7
Step 3. In the 'Threat history' section, click 'Scan now' to scan for viruses on your computer.
Method 3. Format the Infected Device
The format is the process of erasing the existing files on the selected partition or drive. It will certainly remove the virus, too. Since formatting a partition/drive will cause data loss, make sure you don't have any important files stored on the device.
How to Recover Files Deleted/Hidden by Viruses
Don't forget to use a data recovery tool in case the virus deleted or hid your important files on USB and other drives. Using commands can only help remove the virus but can do nothing to restore damaged and lost files. EaseUS file recovery software is able to complete virus file recovery in just three steps.
Learn the 3-step file recovery in this video guide.
How to Prevent Virus or Malware Infections
Except for knowing how to cope with a virus attack, you should also know how to prevent virus infection on your computer or external storage device. For you to protect your computer or USB drives better, here are some feasible tips on virus prevention for you:
Install professional antivirus software on your computer and keep it updated
Be cautious with the origins of the programs you want to install
Avoid suspicious websites and think before you make a click
Make sure the network connection is safe
Besides, regularly making backups of your files with free backup software is also recommended to avoid complete data loss that may be caused by a virus infection.
The Bottom Line
Removing a virus using CMD is a roundabout solution. Yet it works in some cases. If the attrib command fails, try the three more tips provided to get rid of the malicious file. Besides, virus attacks are always accompanied by data loss. In that case, use the hard drive recovery software - EaseUS Data Recovery Software to rescue the lost files as soon as possible.